

I can excuse attempting to compromise millions of computer systems worldwide for nefarious purposes but I draw the line at violating the contributor guidelines of an opensource project.


I can excuse attempting to compromise millions of computer systems worldwide for nefarious purposes but I draw the line at violating the contributor guidelines of an opensource project.


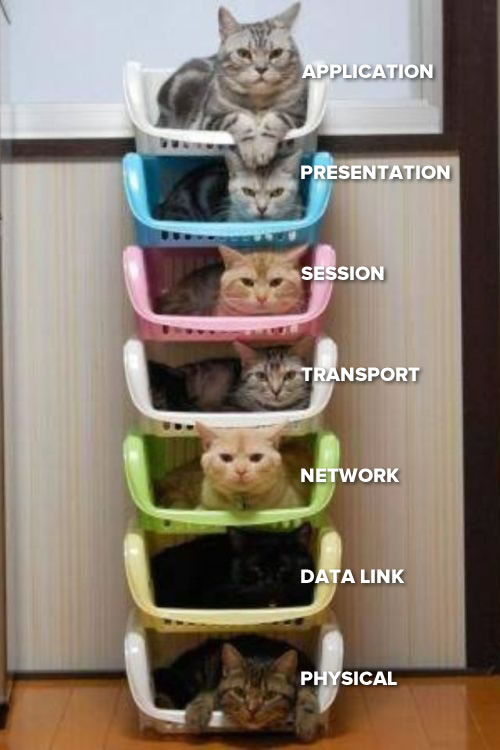
The top cat uses ports to sort messages based on application.

Think pigeon holes, applications usually use protocols which are assigned a number by convention. The application gets it’s message out of it’s assigned ports instead of having to sort through all the messages.


King Slayer vs a King



best guess is the vpn endpoint is blacklisted by google.com with the requests being ignored instead of serving you with a 403 as some sites might. The other geographic google tlds I assume are operating separate blacklists.


Voter registration is public information and sufficient for cold callers.
If you live independently you will inevitably have to make privacy sacrifices for the sake of expediency. Having a bank account is probably going to be one of them. There are many essential services that you use but probably do not think of as an eighteen year old that may share information when you provide for yourself such as your phone carrier, ISP, utilities such as power, water, gas etc, insurance, health services, education or certification providers, employment or recruitment agencies, the list just goes on and you will have to thoroughly evaluate every company you interact with and in many cases there will simply be no realistic privacy respecting option.
Keep fighting to protect your privacy but don’t put an impossible burden on yourself to be perfect. You will make mistakes, you will make compromises, you will probably get spam. Welcome to late stage capitalism.


alias?


They don’t want pirates removing the slot machine monetization from their game for children.


Android is built on linux yet it is increasingly locked down and many phones are extremely difficult to get root access on.
So Valve could have followed the phone ecosystem path and pushed as much of the feature set as proprietary code as possible (binary blob drivers, proton proprietary instead of bsd), replaced pacman with a valve controlled package manager & repos, setup selinux to give users no power to do anything and made the deck only able to secure boot steamOS signed by Valve. Technical users may be able to jail break such a device but the majority would not be inclined to.
Valve’s wisdom here is in realizing that the majority are going to buy their games anyway but if you don’t lock the device down then most of the technical users will also buy most of their games whereas if you have to go out of your way to jail break a device to install something fun then that device basically becomes a piracy only device from that point on.
Linus Torvalds. He’s making a list.


Here is a really interesting video on lightbulbs which goes into how the light bulb cartel standard was more of a min-maxing of lifespan vs energy cost vs brightness than it was planned obsolescence.
I mean you could look at the architecture but all you really needed is a level
I unfortunately can’t speak to this directly as I don’t have direct knowledge of ad blockers.
Yeah me too 
I think the idealization of this kind of spartan living space is basically the same as the cryptobro idealization of unregulated currency.
Over time exposure to reality will result in making compromise after compromise to solve each problem that arises until you have reinvented from first principles the very same standards that everyone else in society already arrived at.


I just tossed a coin out the window at the nearest child and told them to fetch me the plumpest turkey in the butcher’s window.


It’s token DRM for publisher box checking. It shouldn’t need to there but I appreciate that they almost make a point of doing the bare minimum.
Not all unencrypted apps are equivalent. Not wanting to use something owned by meta under any circumstances is completely reasonable.


I did the same thing starting probably around the same time as you except that did it start working for me 5 years ago and I haven’t gone back to windows.
It’s just what cars look like when they are designed for functionality rather than as a statement about the owner’s masculinity.


There are two doors, one is labelled “Leopards that will eat your face” the other “Cat cafe” both lead into the same leopard cage.
“if” gcc had a Ken Thompson hack how do you secure checks notes anything